Latest Update 12/19/19: Commencing January 1, 2020, Providers must submit claims to Medicare with the Medicare Beneficiary Identifier (MBI) regardless of the date of service.
Beginning January 1, 2020:
- Medicare will reject claims submitted with the old Health Insurance Claim Numbers (HICNs) with several exceptions.*
- Medicare will reject all eligibility transactions submitted with HICNs.
- Customer service representatives on the phone will not be able to identify patients using the HICN.
- Since the MBI has more alpha characters than the HICN, CGS suggests using their tool to convert the MBI into characters to use on the telephone number pad for IVR inquiries before calling. The tool can be located here.
- Other MACS have a conversion tool, too.
- The MBI will not be on the Medicare Summary Advice or 835 if the HICN was submitted on the claim and the claim denies for submitting the claim with the HICN.
If you do not use MBIs on claims on and after January 1, 2020 you will receive:
- Electronic claims reject codes: Claims Status Category Code of A7 (acknowledgment rejected for invalid information), a Claims Status Code of 164 (entity’s contract/member number), and an Entity Code of IL (subscriber)
- Paper claim denial codes: Claim Adjustment Reason Code (CARC) 16 “Claim/service lacks information or has submission/billing error(s)” and Remittance Advice Remark Code (RARC) N382 “Missing/incomplete/invalid patient identifier”
Railroad Medicare beneficiaries will have the same format of numbers and will not be identifiable by their MBI. The patient cards will have a Railroad Retirement Board logo on them.
Medicare Advantage plans have their own subscriber identification numbers which are not MBIs.
Quadax EDI has updated several existing edits to accommodate the MBI and edit the HICN for the submission date of January 1, 2020 and after.
*For more information, see the MLN Matters Article.
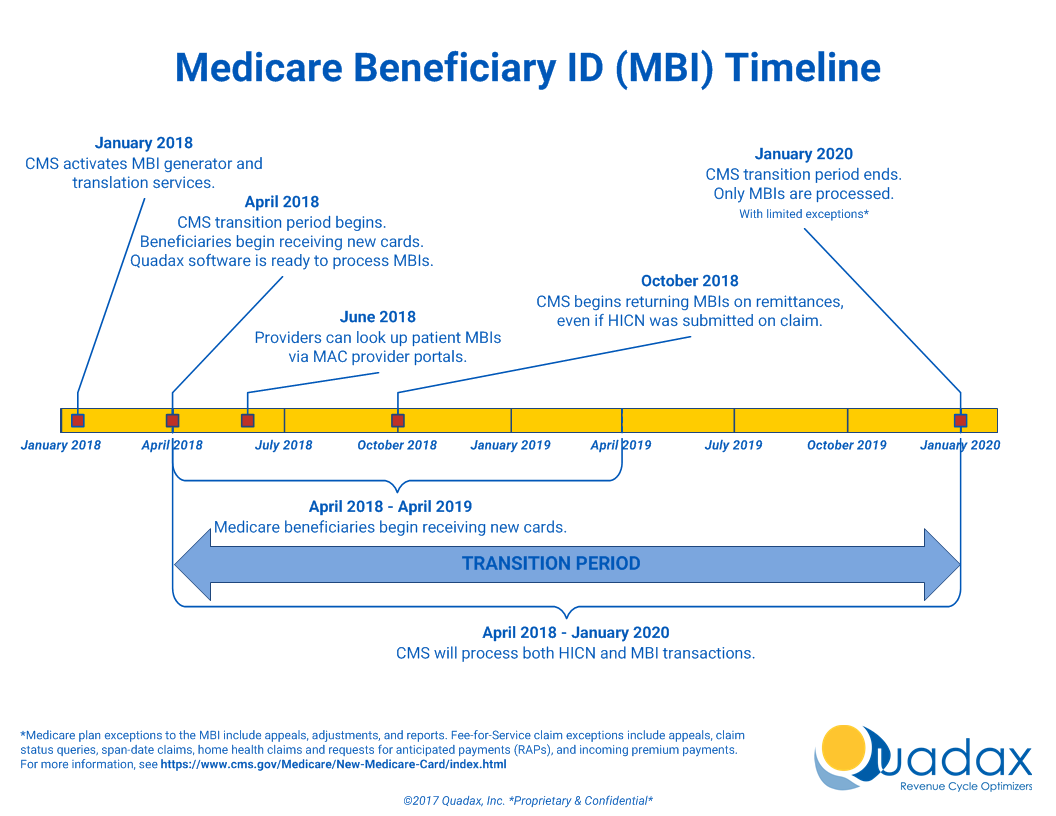
The Medicare Access and CHIP Reauthorization Act (MACRA) of 2015 mandates that the Centers for Medicare & Medicaid Services (CMS) remove Social Security Numbers (SSNs) from all Medicare cards by April 2019. All Medicare accounts will be updated with a new Medicare Beneficiary Identifier (MBI) beginning in April 2018, which will replace the SSN-based Health Insurance Claim Identifier (HICN). From April 1, 2018, through December 31, 2019, a transition period will be in place, during which both the MBI and HICN are accepted for Medicare transactions.
To prepare for this change, Quadax will be updating several elements of our software by April 1, 2018. These updates will ensure that Quadax’s suite of Revenue Cycle Management products can seamlessly make the switch to the new MBI.
This page will be a resource for information on Quadax’s efforts to help our clients with the shift to MBIs.
- The MLN Fact Sheet, “Transition to New Medicare Numbers and Cards” published by CMS October 2017 answers a number of questions about using the new identifier, and gives information about the format for the MBI, which will be 11 alpha-numeric characters.
- To assist in communicating the change to patients, CMS created a one minute video to explain when and how patients will receive their new card. Consider playing the New Medicare Cards Are Coming video in your waiting room.
- 6/18/2018: MBI Lookup Tool Now Available through Your MAC All Medicare Beneficiary Identifier (MBI) lookup tools are ready for use on Medicare Administrative Contractor (MAC) secure portals. If you don’t already have access, sign up for your MAC’s portal to use the tool. Submit four data elements about your patient through the tool, and it will return the MBI if the new Medicare card has already been mailed.
- Medicare is mailing new cards in phases by geographic location. For more information about the MBI, read the MLN Matters® Special Edition Article. Medicare is currently mailing new cards to people who:
- Live in Alaska, American Samoa, California, Delaware, District of Columbia, Guam, Hawaii, Maryland, Northern Mariana Islands, Oregon, Pennsylvania, Virginia, and West Virginia
- Get Railroad Retirement Board benefits
- Are newly entitled to Medicare